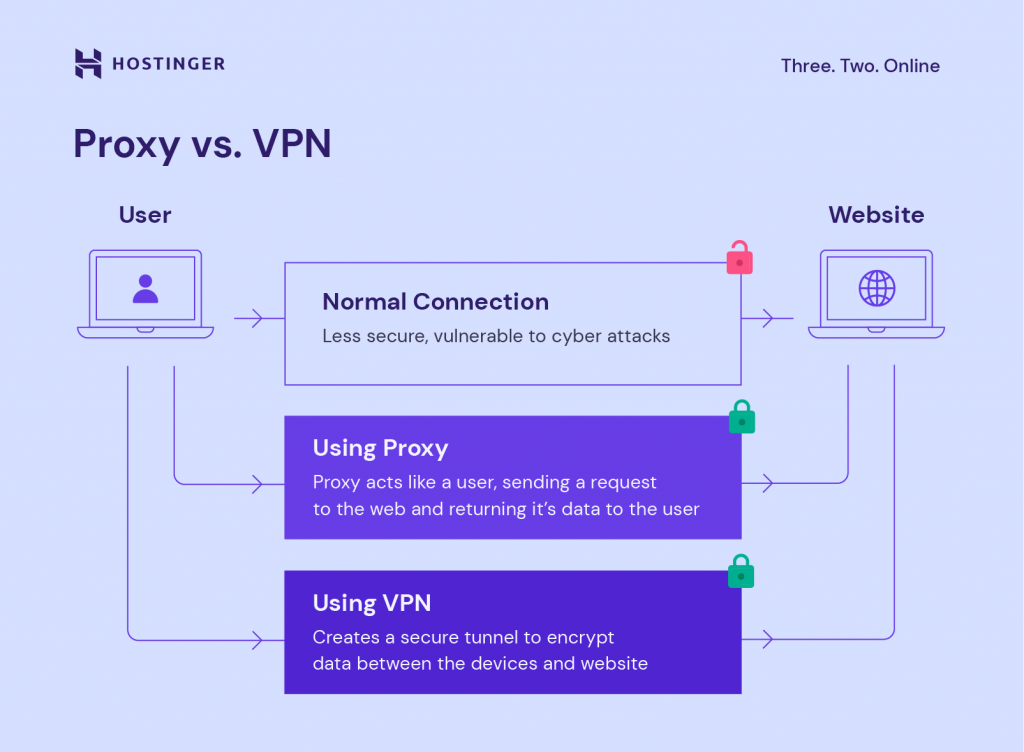
Proxies and Configurations Used for Credential Stuffing Attacks on Online Customer Accounts - HS Today
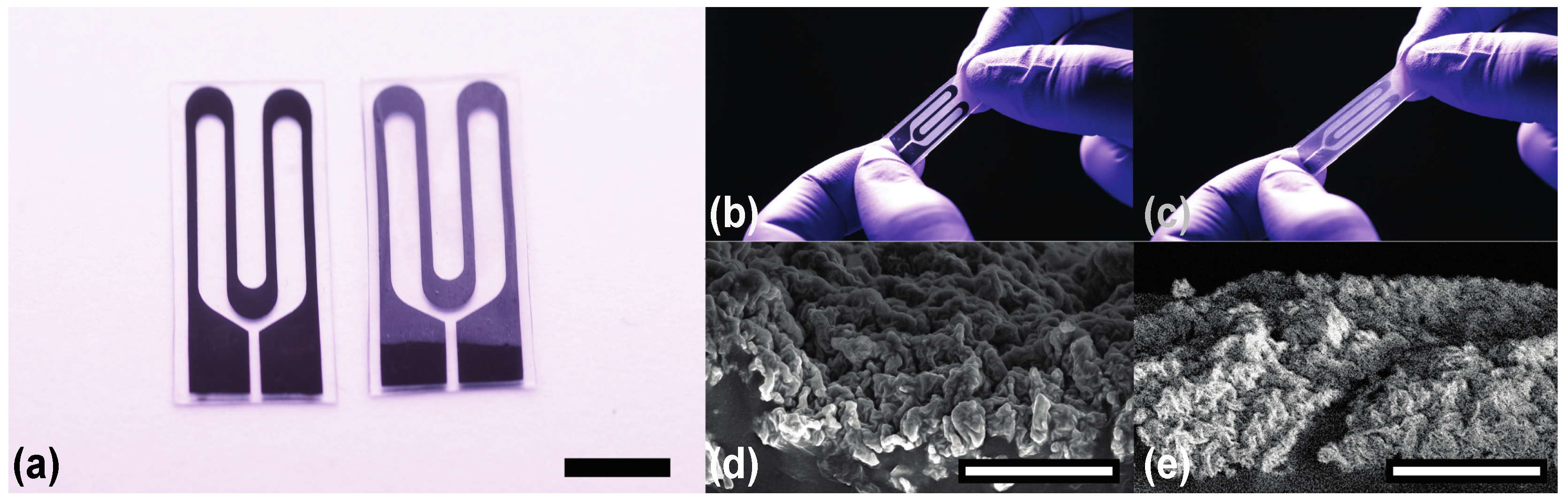
Materials | Free Full-Text | The Effect of Encapsulation on Crack-Based Wrinkled Thin Film Soft Strain Sensors

How to Chain Proxies to Mask Your IP Address and Remain Anonymous on the Web « Null Byte :: WonderHowTo

Measuring the Particle Packing of l-Glutamic Acid Crystals through X-ray Computed Tomography for Understanding Powder Flow and Consolidation Behavior | Crystal Growth & Design

VA proposes updates to disability rating schedules for respiratory, auditory and mental disorders body systems - VA News


![Hacking clients with WPAD (web proxy auto-discovery) protocol [updated 2021] | Infosec Resources Hacking clients with WPAD (web proxy auto-discovery) protocol [updated 2021] | Infosec Resources](https://resources.infosecinstitute.com/wp-content/uploads/2014/07/013021-5.png)





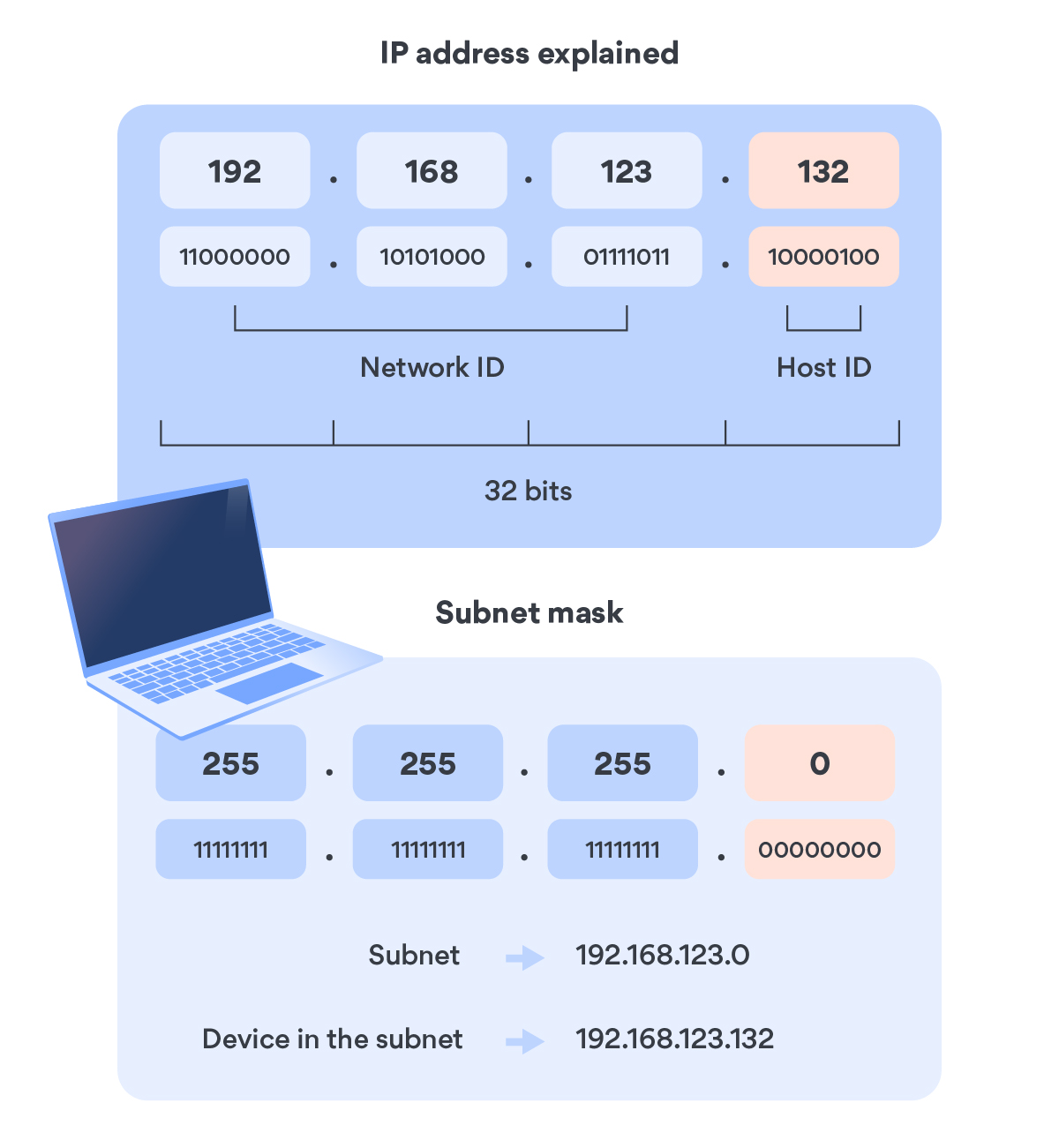



![Hacking clients with WPAD (web proxy auto-discovery) protocol [updated 2021] | Infosec Resources Hacking clients with WPAD (web proxy auto-discovery) protocol [updated 2021] | Infosec Resources](https://resources.infosecinstitute.com/wp-content/uploads/2014/07/013021-1.png)